The GMX hacker who stole $40 million in crypto has started returning the funds.
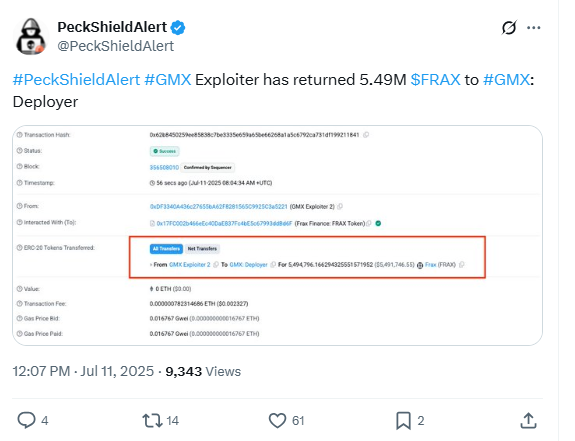
The person behind the GMX exploit wrote an on-chain message on July 11 saying, “Ok, funds will be returned later.” Blockchain security firm PeckShield flagged the message.
This message came after the GMX team offered a $5 million white hat bounty in exchange for returning the funds.
The bounty was set at 10% of the stolen amount. GMX published its offer through an on-chain message and a public statement.
The hacker used the same address labeled “GMX Exploiter 2” to send the reply. PeckShield confirmed the address activity. This exploit targeted GMX v1, a decentralized exchange on Arbitrum.
First Transfers: Hacker Returns $9 Million in ETH
Less than an hour after the on-chain message, the GMX hacker returned 2,990 ETH, worth around $9 million, to the GMX-provided address. PeckShield confirmed the transaction on Ethereum, not Arbitrum.
The funds were returned to the wallet listed in GMX’s on-chain instructions. The GMX team had disabled minting, trading, and redeeming on GMX v1 contracts earlier in the week to stop the attack.
The GMX exploit involved manipulating the value of GLP tokens inside a liquidity pool on the Arbitrum blockchain.
$10.5 Million in FRAX Tokens Returned in Two Transfers
The GMX hacker sent more funds later the same day. First, $5.5 million in FRAX tokens was returned. Later, another $5 million in FRAX came back. PeckShield confirmed both transfers.
With these two transactions, the crypto returned totaled around $20 million, or half the stolen funds. The GMX team received all transfers in the addresses it provided.
FRAX is a stablecoin. These were among the various assets drained from the liquidity pool during the GMX exploit.
GMX Team Issues 48-Hour Legal Warning Before Refund Started
Before the refund, the GMX team issued a warning. In an on-chain message, they told the GMX hacker that legal action would follow if funds were not returned within 48 hours.
They also offered to prove the bounty was from clean funds. “The white hat bug bounty of $5 million continues to be available,” the GMX team wrote. They stated this would help the hacker avoid risks tied to stolen funds.
The message allowed the hacker to keep 10% of the stolen amount—$5 million—if they returned the other 90%.
GMX Exploit Details and Platform Response
The GMX exploit happened on July 10, targeting the first version of the trading platform deployed on Arbitrum. The hacker used a design flaw to manipulate GLP token values, draining crypto assets.
The GMX v1 contracts on both Arbitrum and Avalanche were paused to prevent further impact. The GMX team said they are working on security reviews.
At the time of writing, the GMX hacker had returned $20 million in total. The remaining $20 million had not been recovered.
The GMX team and PeckShield are monitoring the wallet activity. The final outcome remains pending.
Disclosure:This article does not contain investment advice or recommendations. Every investment and trading move involves risk, and readers should conduct their own research when making a decision.
Kriptoworld.com accepts no liability for any errors in the articles or for any financial loss resulting from incorrect information.


