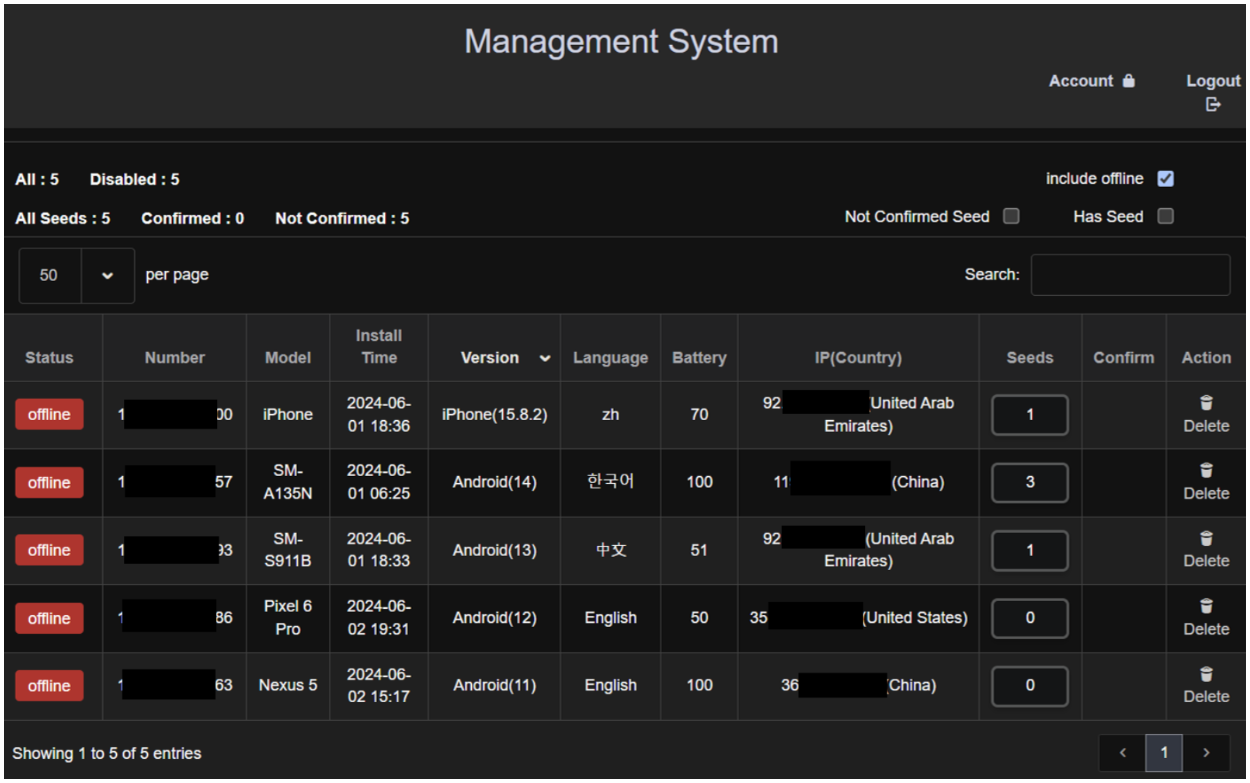
A new type of Android malware named SpyAgent has been discovered, which can steal private keys from screenshots and images stored on phones.
How SpyAgent works?
SpyAgent was identified by McAfee, which explains that the malware uses a technology called optical character recognition, the OCR.
This technology allows it to scan images and extract text from them, including sensitive information like private keys.
The malware spreads through malicious links sent via text messages, and when an unsuspecting user taps on one of these links, they are redirected to a fake website that looks legitimate.
The site then prompts the user to download an application that appears trustworthy, but in reality, it is SpyAgent. Once installed, the malware compromises the user’s phone.
McAfee reports that these applications are often disguised as banking apps, government services, or streaming platforms.
Users are then asked to grant permissions that allow the malware to access their contacts, messages, and local storage.
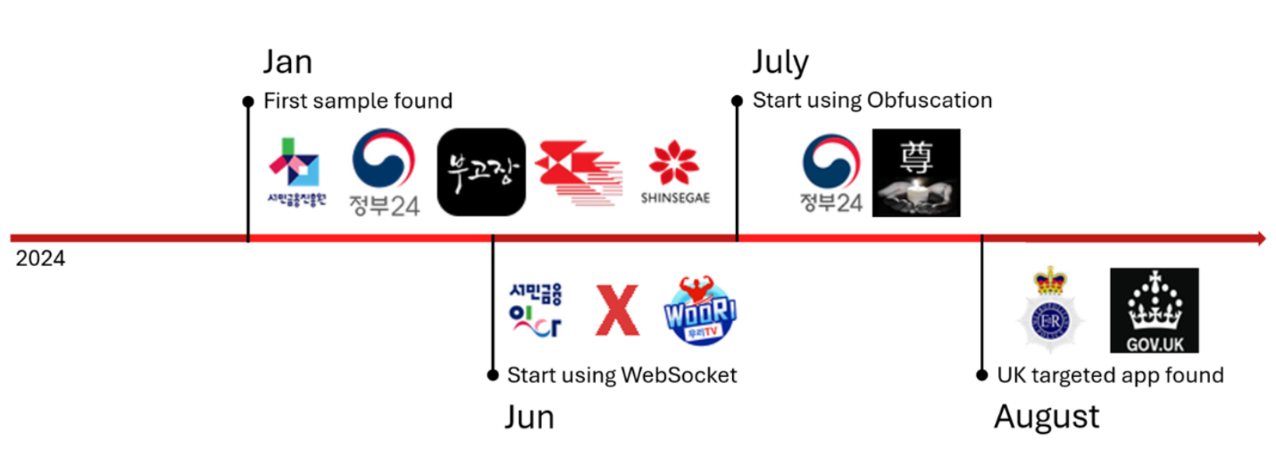
Right now SpyAgent is primarily targeting users in South Korea and has been found in over 280 fraudulent apps.
Malware threats in 2024, a big issue
The rise of malware attacks is an ever growing concern. In August, another malware called Cthulhu Stealer was discovered, targeting MacOS systems.
Similar to SpyAgent, Cthulhu Stealer pretends to be a legitimate software application and steals personal information, including MetaMask passwords and private keys for cold wallets stored on desktops.
Google Chrome vulnerability threats crypto users
In the same month, Microsoft uncovered a vulnerability in Google Chrome that was likely exploited by a North Korean hacker group known as Citrine Sleet.
This group created fake cryptocurrency exchanges and sent fraudulent job applications to unsuspecting users.
Those who followed through with the job application process unknowingly installed malware that could remotely control their systems and steal private keys.
The mentioned Chrome bug has since been patched, but the increase in malware attacks led the FBI to issue a warning about the activities of the North Korean hacking group.